Tools Used
- OPNsense Firewall
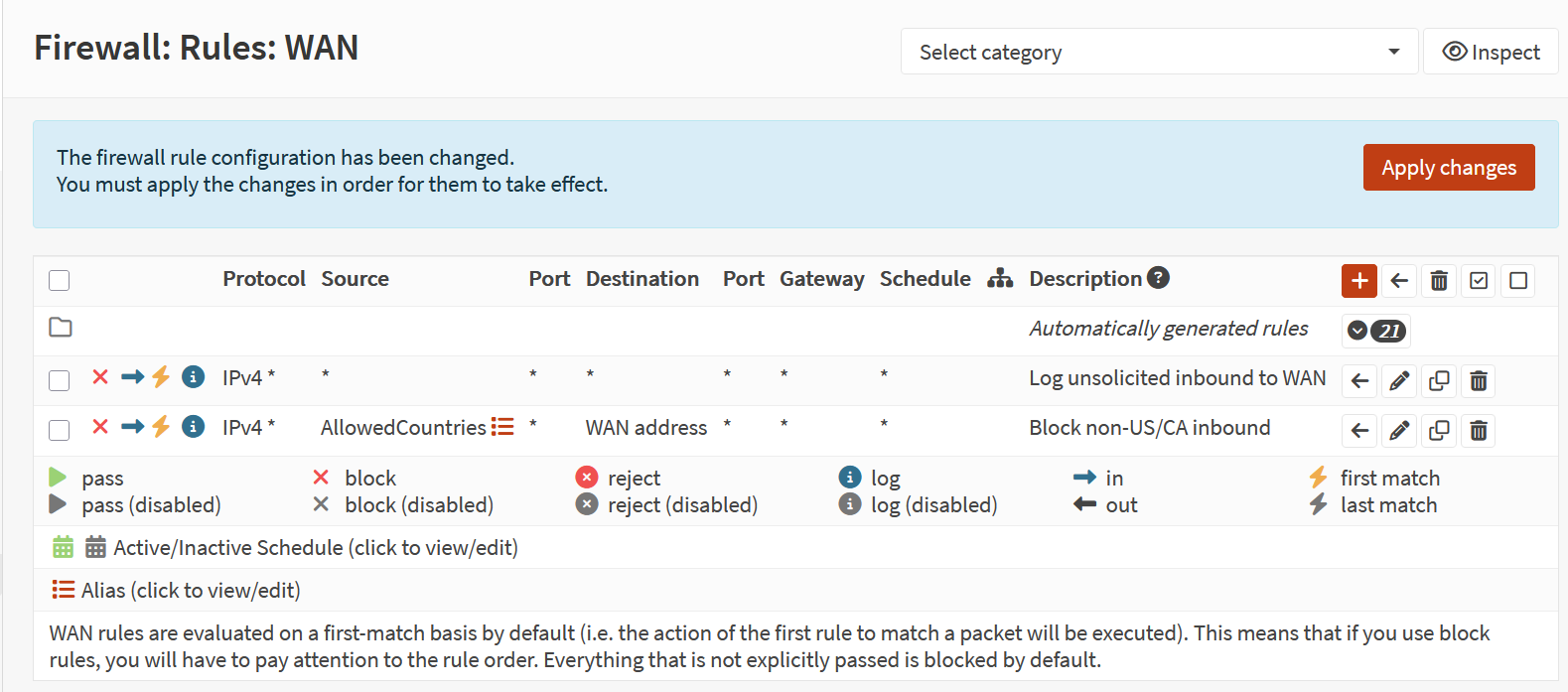
- Firewall Rules (WAN → LAN)
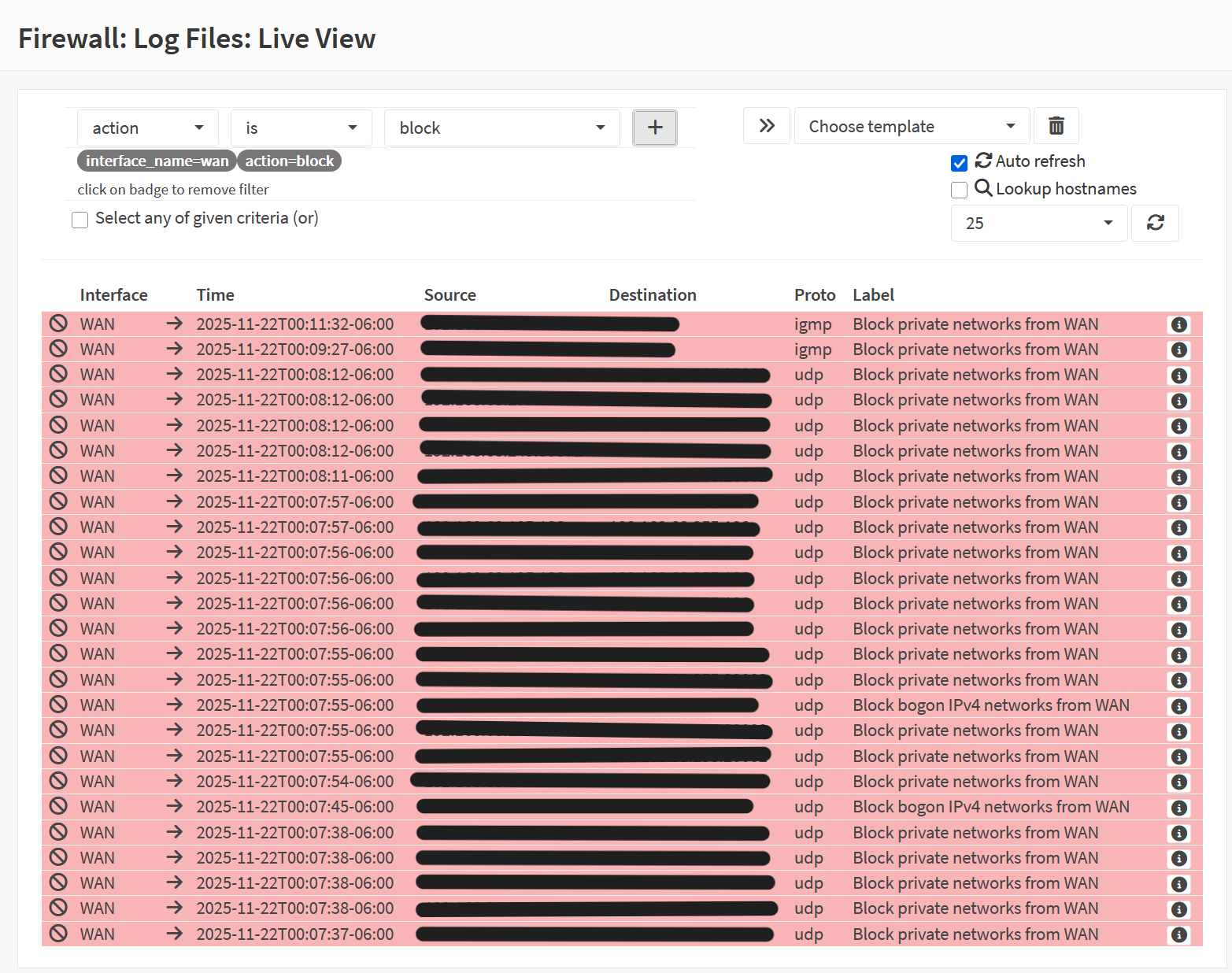
- Log Viewer
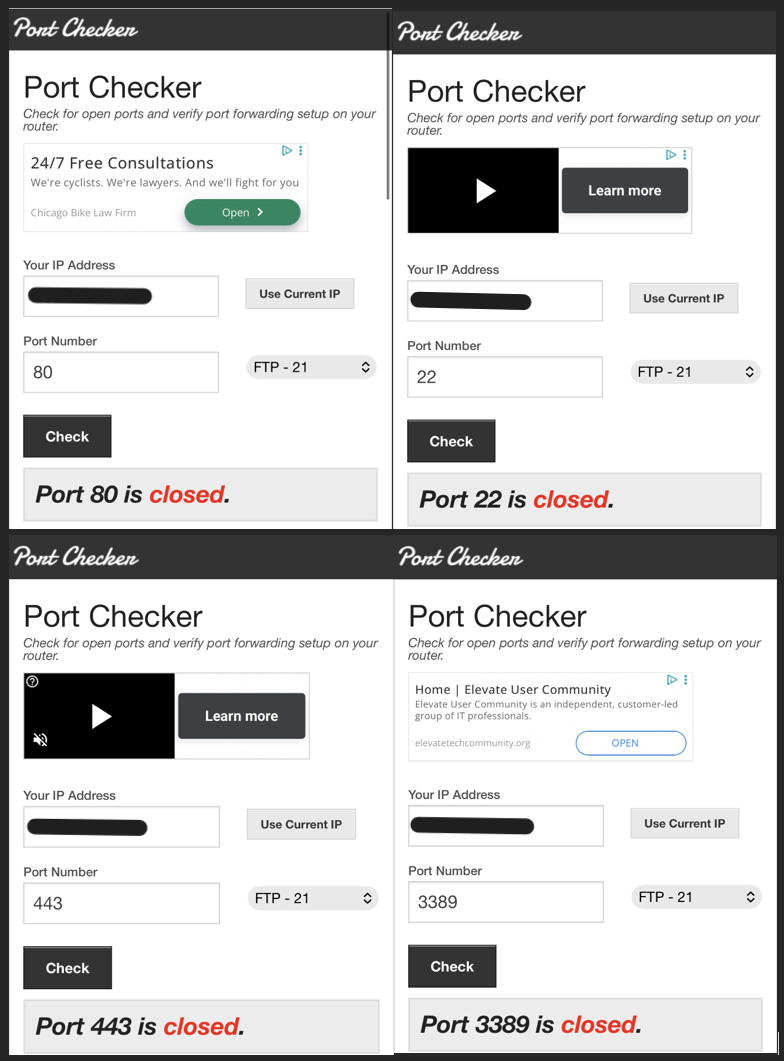
- Diagnostics: Port Scan / External Reachability Tests
Steps Taken
- Verified default deny posture on WAN rules.
- Added explicit block/log rules for clarity.
- Tested inbound reachability from external host (SSH/HTTP attempts).
- Confirmed traffic blocked and logged.
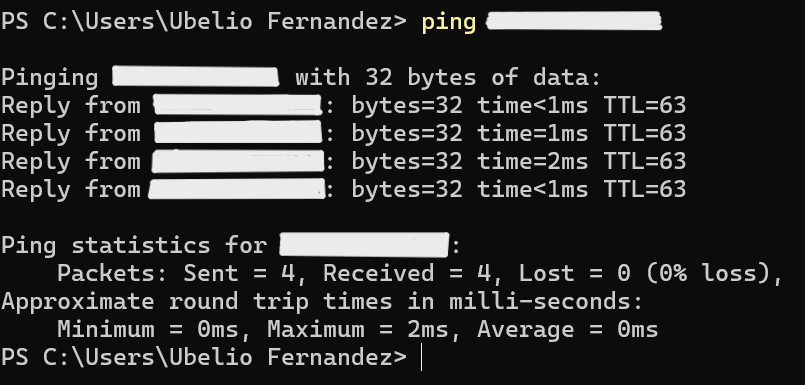
- Validated LAN services remained accessible internally.
Screenshot: WAN Rules
Screenshot: Inbound Attempt
Screenshot: Blocked Inbound Traffic
Screenshot: LAN Access
Outcome
Inbound traffic denied by default, with explicit block/log rules documented. External scans confirmed no exposed services. Internal LAN access unaffected. This demonstrates secure baseline posture.