🏗️ Home Lab Configuration
This lab is engineered to simulate enterprise-grade identity, security, and automation workflows. Every component is selected for performance, resilience, and real-world fidelity—supporting certification prep, documentation, and advanced experimentation.
🎯 Lab Goals
- Build enterprise-grade lab projects for:
- Cybersecurity (Defender, SIEM, Security Onion)
- Endpoint protection and response
- Systems administration (AD, DNS, DHCP, automation)
- Network segmentation and Zero Trust architecture
🧰 Equipment Breakdown
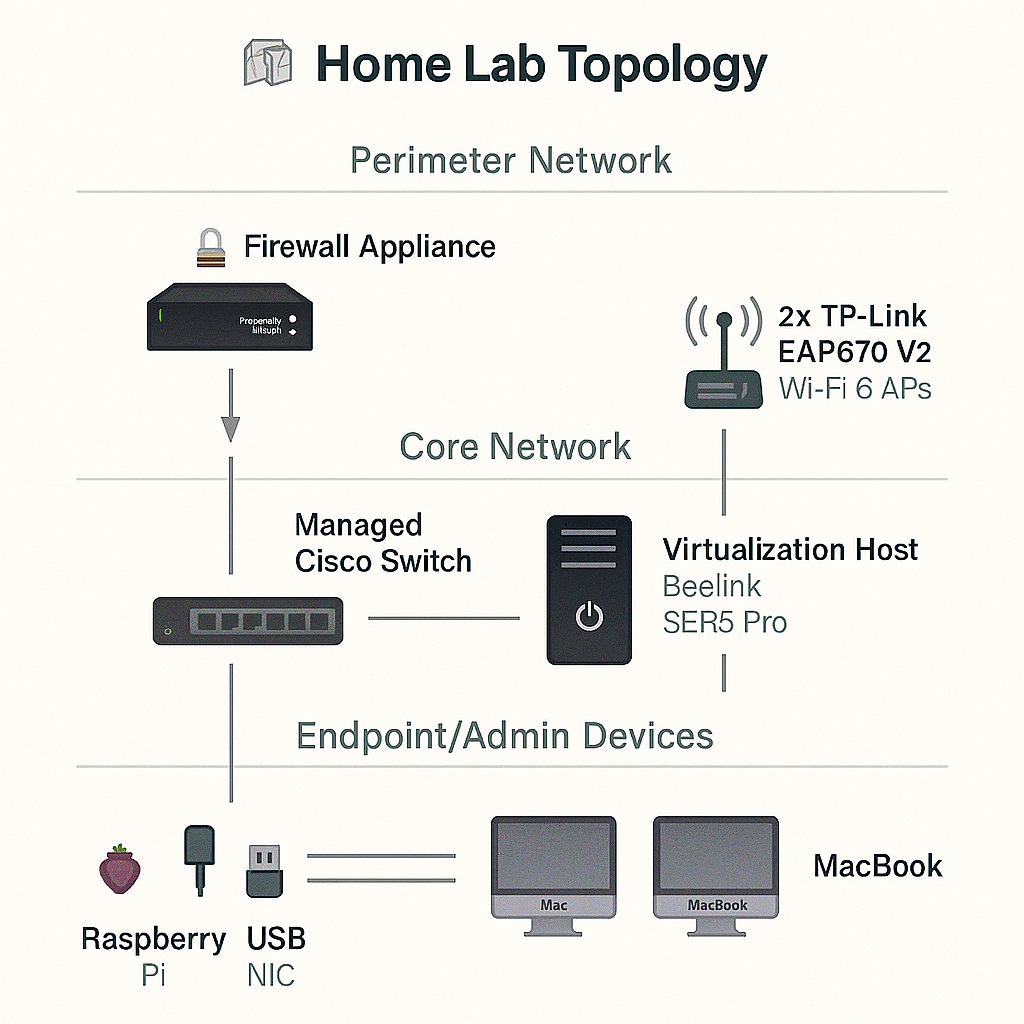
🔐 Firewall Appliance: Intel N150 (4-core, 6W TDP), 6× Intel i226-V 2.5GbE NICs, 32GB DDR5 RAM, 1TB NVMe SSD. Runs pfSense/OPNsense for perimeter control, VLAN routing, and Zero Trust simulation.
🧩 Core Switching – Managed Cisco Switch: Serves as the VLAN backbone and SPAN port provider for Security Onion, Defender, and SIEM traffic capture.
📡 Wireless Infrastructure – 2× TP-Link EAP670 V2: Wi-Fi 6 APs with Omada controller support. VLAN-tagged SSIDs for lab, guest, IoT, and admin segmentation.
🧠 Virtualization Host – Beelink SER5 Pro: AMD Ryzen 7 5800H (8C/16T), 64GB DDR4 RAM, 1TB NVMe SSD. Runs Proxmox hypervisor hosting AD, DNS, DHCP, Defender for Endpoint, Security Onion, SIEM, and automation testing.
💻 Endpoint & Admin Devices: MacBook (admin console, remote access, scripting, documentation), iMac (secondary admin, endpoint simulation, monitoring), monitors (BIOS access, VM setup, troubleshooting), external SSDs (VM snapshots, log storage, backup targets).
🔌 USB NIC – Plugable USB 3.0 to Ethernet Adapter: Intel-compatible (ASIX AX88179). Adds second NIC for VLAN trunking, SPAN mirroring, and multi-interface firewalling.
🍓 Raspberry Pi 4: Quad-core ARM Cortex-A72, 4GB or 8GB LPDDR4 RAM. Used as a lightweight DNS sinkhole, honeypot, automation node, or remote sensor.
🗺️ Topology Diagram
A visual diagram showing how all components connect—firewall, switch, hypervisor, endpoints, wireless, and sensors. It illustrates ab architecture.