Tools Used
- OPNsense Firewall
- Web GUI access
- Configured VLANs from previous labs
- Client devices for validation tests
- Browser + screenshot tool
Steps Taken
- Opened Firewall → Rules for each VLAN interface.
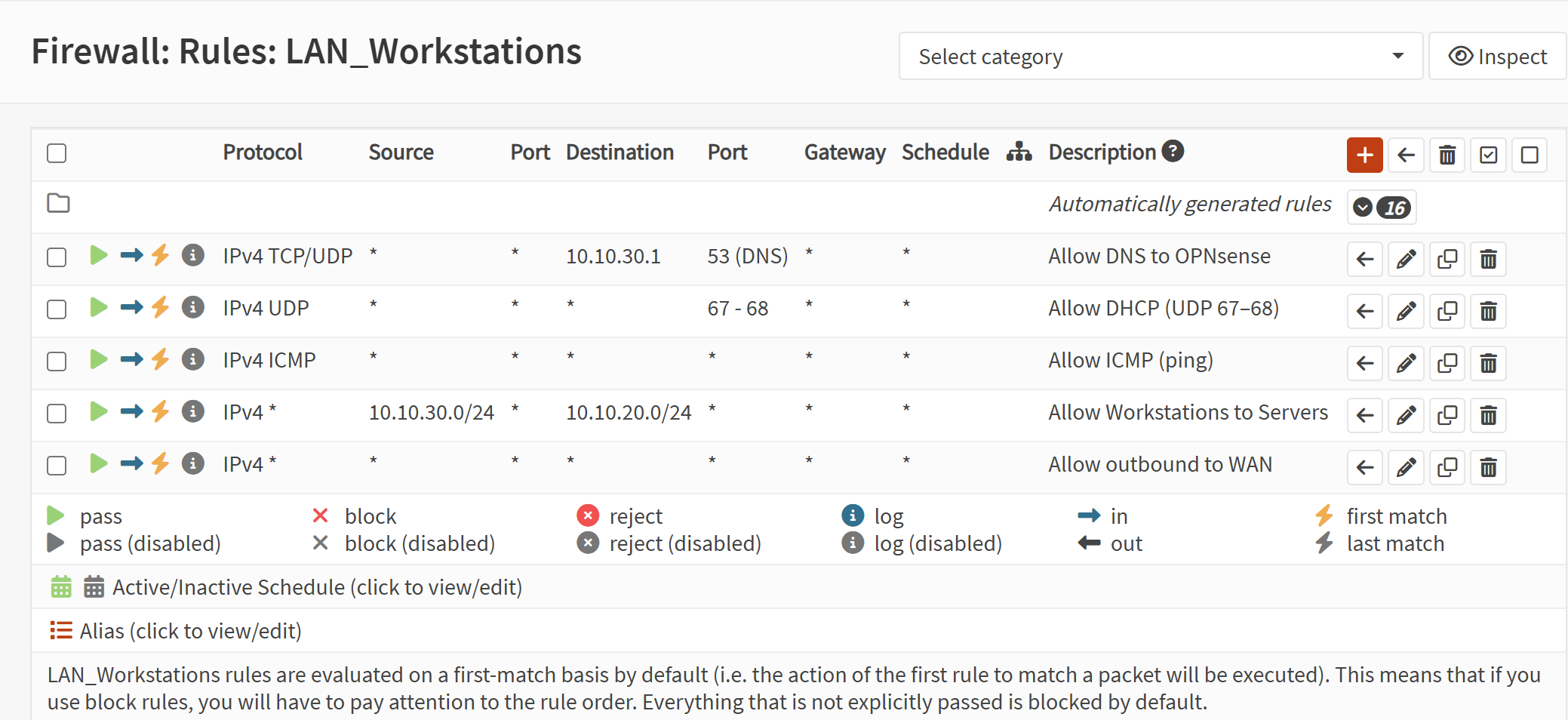
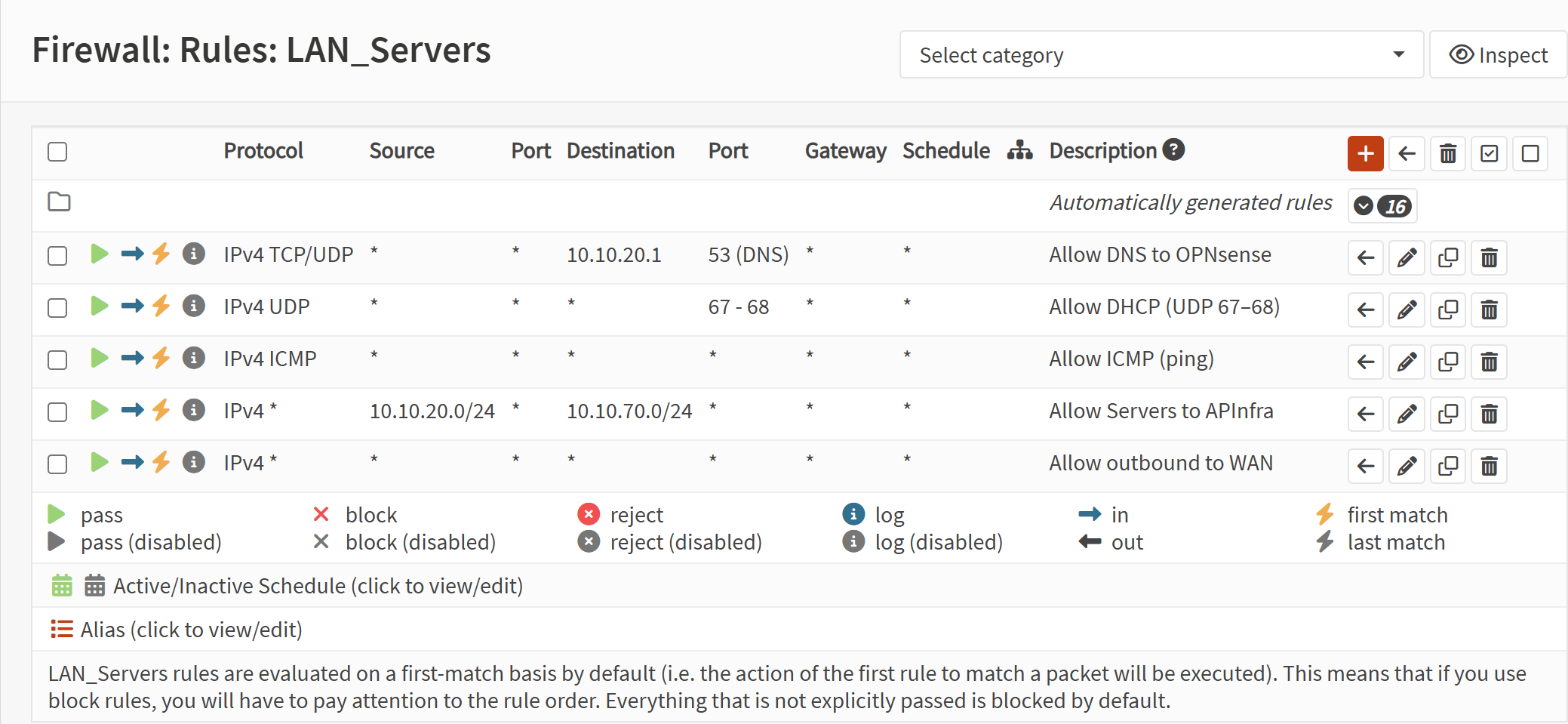
- Created allow rules for:
- Workstations → Servers
- Management → All VLANs
- Servers → APInfra
- Ensured each interface ends with a block-all rule with logging enabled.
- Applied changes and verified rule order.
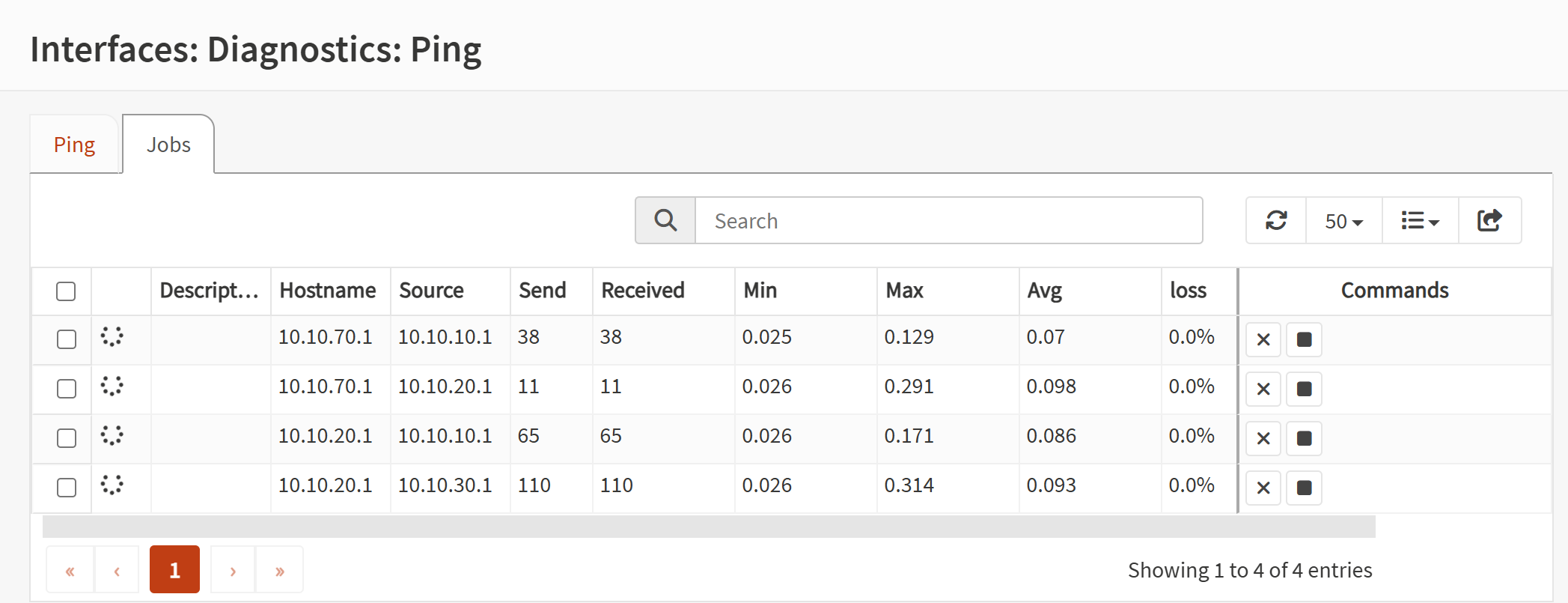
- Validated allowed paths using ping and service tests.
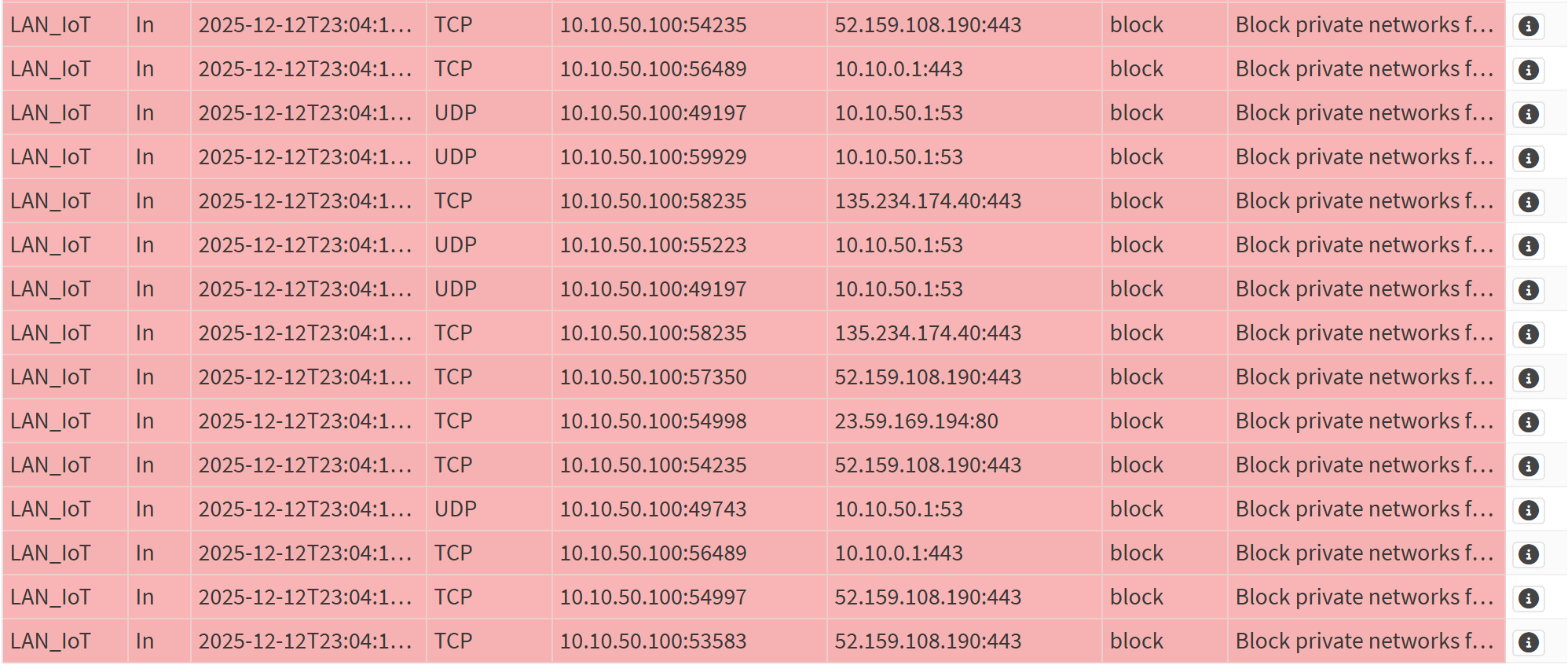
- Generated intentional blocked traffic to confirm segmentation enforcement.
Screenshot: Workstations VLAN Rules
Screenshot: Management VLAN Rules

Screenshot: Servers VLAN Rules
Screenshot: Allowed Communication Tests
Screenshot: Blocked Traffic Logs
Outcome
This lab establishes intentional, policy-driven inter-VLAN communication. Workstations can reach servers, management can reach all VLANs, and servers can reach APInfra. All other cross-VLAN traffic is explicitly blocked and logged. Validation confirmed that allowed paths function correctly while unauthorized attempts are denied and visible in the firewall logs. This enforces a clean, business-aligned segmentation model.