Tools Used
- OPNsense Firewall
- Firewall Rules (LAN → WAN)
- Diagnostics: Ping/Traceroute
- Log Viewer
Steps Taken
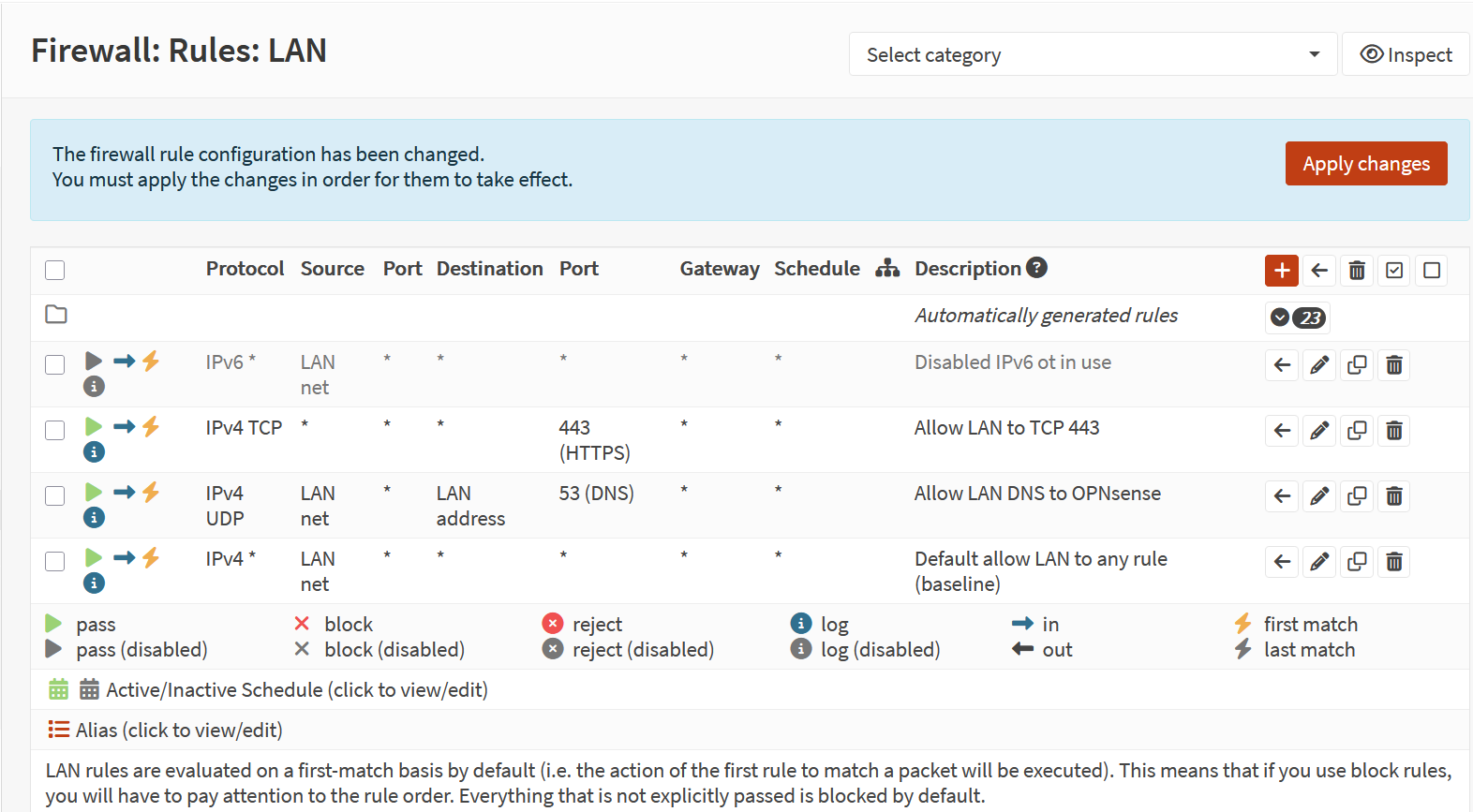
- Created explicit allow rules for HTTPS (TCP/443) and DNS (UDP/53).
- Added final block/log rule for all other LAN → WAN traffic.
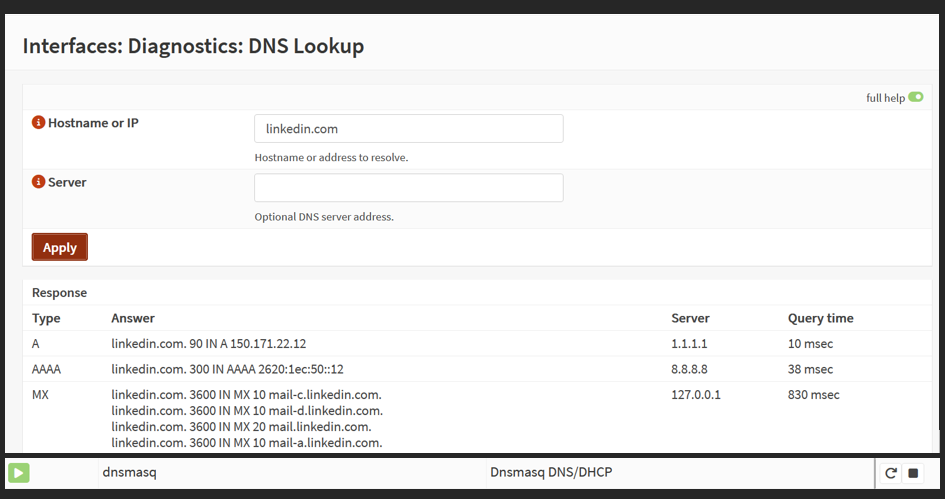
- Validated HTTPS browsing and DNS lookups worked.
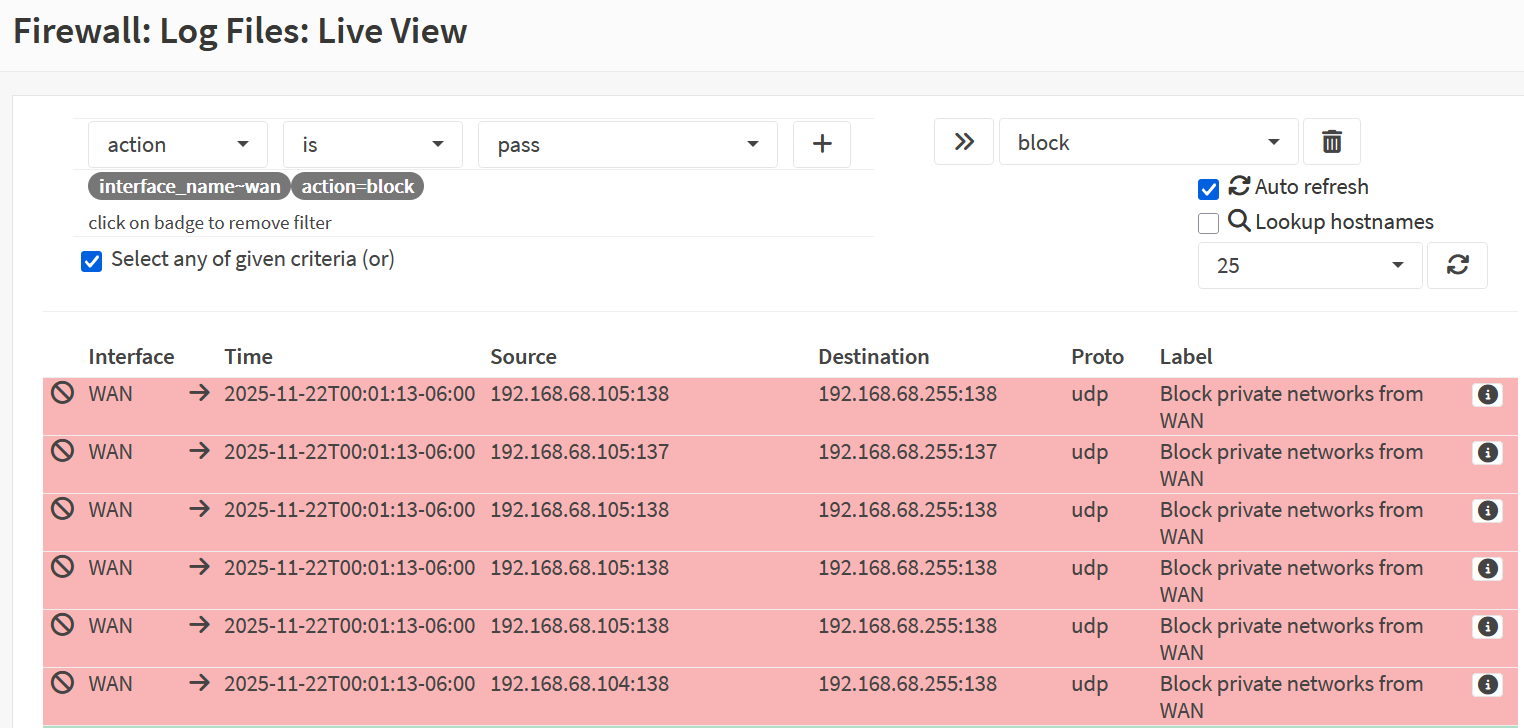
- Confirmed non-allowed outbound traffic was blocked and logged.
Screenshot: LAN Rules
Screenshot: HTTPS Allowed
Screenshot: DNS Allowed
Screenshot: Blocked Traffic
Outcome
Outbound traffic restricted to HTTPS and DNS only. All other traffic blocked and logged, demonstrating least-privilege enforcement.