Challenge
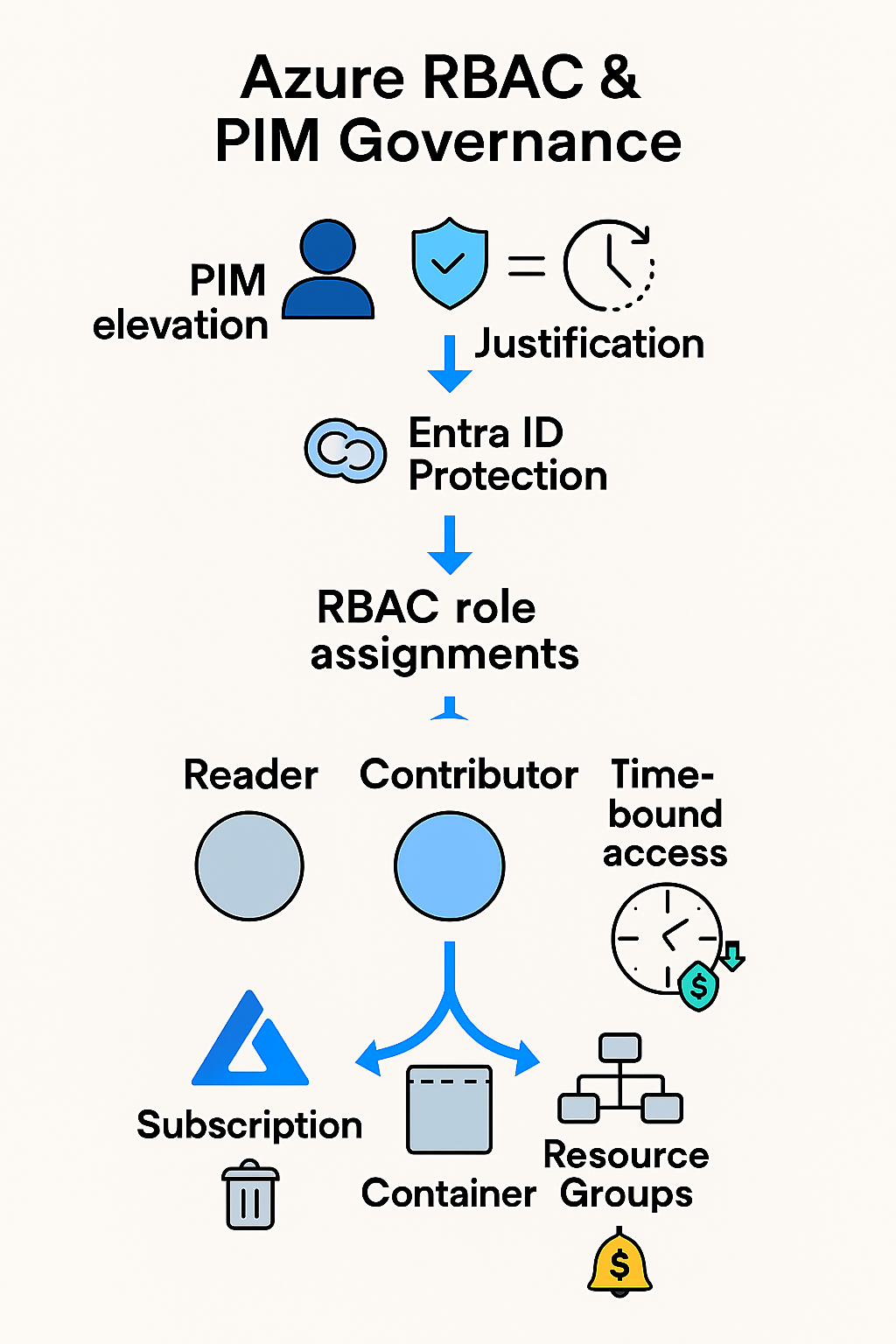
Developers had unrestricted access to Azure subscriptions, containers, and resource groups—posing a risk of compromise and misconfiguration. The goal was to enforce least privilege, deploy just-in-time access, and eliminate unnecessary cloud spend.
Tools & Technologies
- Azure Role-Based Access Control (RBAC)
- Microsoft Entra Privileged Identity Management (PIM)
- Azure Portal & Subscription Management
- Audit Logs & Access Reviews
- Cost Management + Billing
Implementation
- Audited existing access across subscriptions, containers, and resource groups
- Defined custom roles and assigned least privilege access based on job function
- Enabled PIM for Azure resource roles with MFA, justification, and time-bound elevation
- Removed excessive permissions from developer accounts
- Deleted unused subscription that was incurring unnecessary costs
- Validated access flows and monitored activations via audit logs
Architecture Diagram
Impact
- Enforced least privilege across Azure resources
- Reduced risk of compromise and misconfiguration
- Enabled secure, just-in-time access for privileged roles
- Eliminated unnecessary cloud spend by removing unused subscriptions