Challenge
To strengthen identity protection and reduce reliance on insecure MFA methods, our organization needed to enforce phishing-resistant authentication across all users. The rollout had to be staged to minimize disruption and supported by helpdesk onboarding.
Tools & Technologies
- Microsoft Entra Admin Center
- Authentication Methods Policy
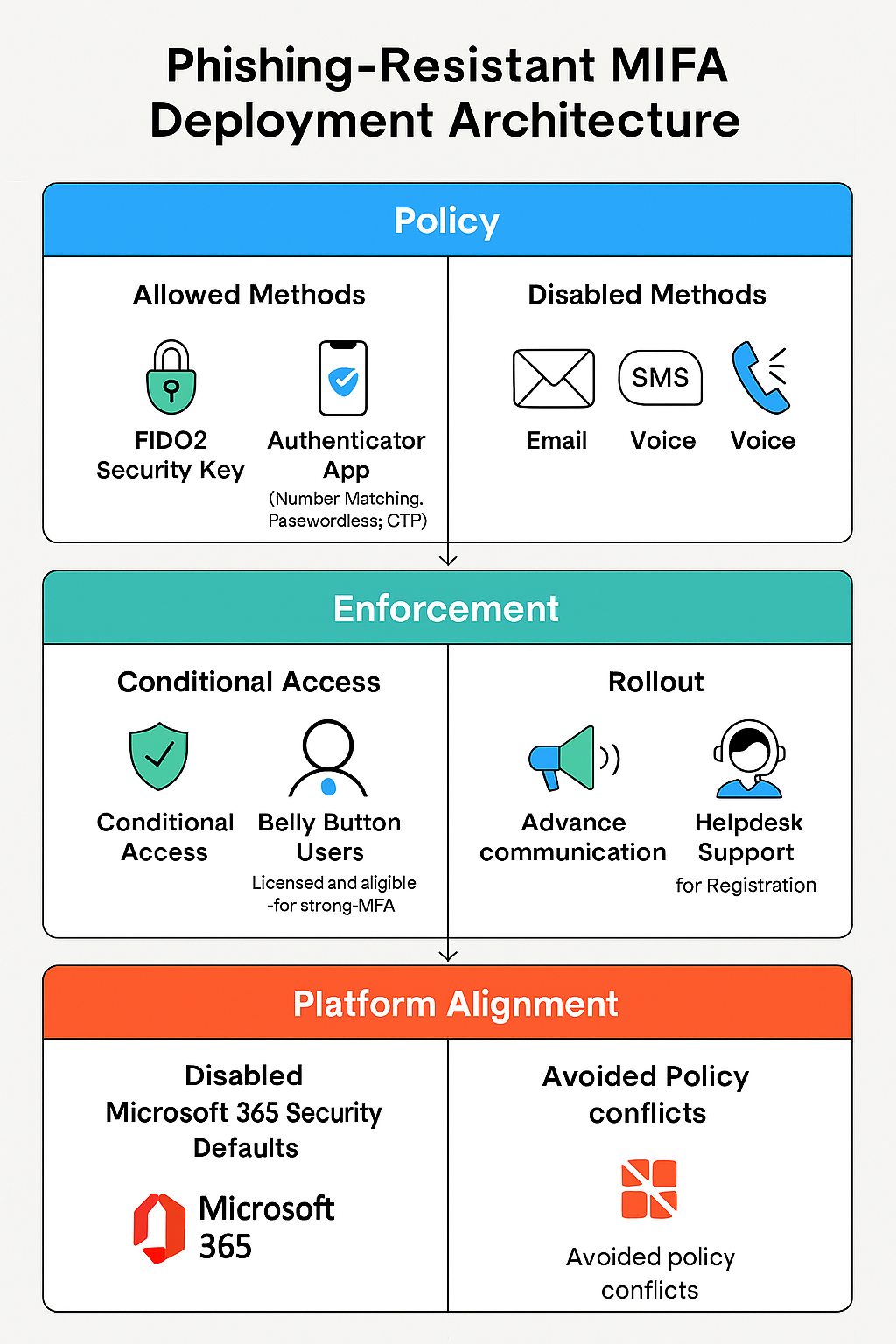
- FIDO2 Security Keys
- Microsoft Authenticator App (Number Matching, Passwordless, OTP)
- Conditional Access Policy
- Helpdesk Registration Support
Implementation
- Configured Authentication Methods Policy to allow only FIDO2 and Microsoft Authenticator
- Enabled number matching, passwordless sign-in, and 6-digit OTP
- Disabled email, SMS, and voice call MFA methods
- Created Conditional Access policy targeting licensed “belly button” users
- Staged rollout with advance communication and helpdesk support
- Assisted users with registration of secure authentication methods
- Disabled Microsoft 365 security defaults to avoid policy conflicts
Architecture Diagram
Impact
- Improved authentication security with phishing-resistant methods
- Reduced reliance on insecure MFA factors
- Minimized disruption through staged rollout and helpdesk support
- Aligned authentication strategy with Microsoft best practices